6 Signs Your Business Needs a vCISO or a Fractional CISO
Cyber risk has quietly become a leading barrier to business growth.
A recent PwC survey found that 58% of CEOs consider cyberattacks a very serious threat to their business operations.
Yet most small and mid-sized businesses still treat it as a technical problem instead of a leadership priority.
As digital operations expand and regulations tighten, even strong IT teams struggle to keep pace without strategic oversight.
A Virtual or Fractional Chief Information Security Officer provides growing companies with that leadership while keeping costs under control.
In this guide, you’ll find six signs your organization may be at the stage where cybersecurity leadership is no longer optional, and how a vCISO can fill that gap effectively.
P.S. Need expert cybersecurity leadership without full-time cost? Alpha Apex Group connects you with seasoned vCISOs and fractional CISOs who deliver enterprise-grade strategy, compliance, and risk management tailored to your business.
Why Cyber Leadership Is No Longer Optional
Cyber threats have evolved into serious business risks. The average cost of a data breach reached $4.9 million in 2024, up nearly 10% from the previous year. Small and mid-sized companies are now prime targets. They are facing attacks four times more often than large enterprises.
Yet roughly 64% of SMBs still operate without a Chief Information Security Officer due to cost constraints. The result is a dangerous gap: threats are rising faster than leadership capacity to manage them.
A modern Chief Information Security Officer provides governance, risk management, and strategic oversight of cybersecurity. They ensure that security controls and policies align with business goals, compliance requirements, and industry frameworks.
Here’s a short explainer video for more details:
Cybersecurity leadership has become essential because clients, partners, and insurers increasingly demand proof of a strong security posture. A single incident can cause fines, lost trust, and long-term damage. Security is now a board-level priority, and companies without experienced oversight risk being blindsided by avoidable threats.
What a vCISO or Fractional CISO Actually Does
A Virtual Chief Information Security Officer (vCISO) delivers executive-level cybersecurity leadership on a flexible basis. These professionals perform the same functions as full-time CISOs, focusing on governance and strategy rather than daily IT operations.
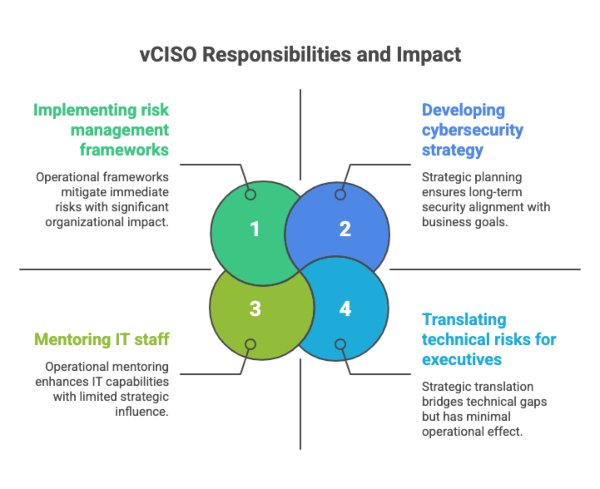
Core duties include developing a cybersecurity strategy, managing risk, ensuring compliance, and preparing for incidents comparable to a full-time CISO.
In practice, a vCISO assesses your security posture, identifies gaps, and creates a security roadmap aligned with business priorities. They implement risk management frameworks, lead cybersecurity awareness training, and translate technical risks into business terms for executives.
Their role extends to mentoring IT staff and helping the organization adopt best practices across access management, threat monitoring, and regulatory compliance. This ensures that cybersecurity becomes a structured, measurable business function rather than an afterthought.
Why More Mid-Sized Companies Are Turning to vCISOs
vCISOs offer speed and depth of experience. They can start within weeks and bring lessons learned from multiple industries, giving mid-sized businesses access to proven frameworks and creative solutions.
As cyber threats grow more sophisticated, many companies now see vCISOs not as optional consultants but as strategic partners who provide cybersecurity leadership equal to full-time executives, without the prohibitive cost.
Pro tip: To speed up your vCISO hiring process, work with a partner that already knows the cybersecurity leadership market inside and out. Alpha Apex Group maintains an 80%+ placement success rate, focuses on matching companies with vetted fractional and vCISOs, and can present qualified candidates within just 72 hours.
Lets now explore the signs that your business is in need of one of these experts.
Sign 1: Your Budget Can’t Justify a Full-Time CISO
Hiring a full-time Chief Information Security Officer is a major financial commitment. Total compensation often exceeds $250,000 per year once salary, benefits, and bonuses are included.
In larger enterprises, senior CISOs can earn an average of $565,000 or more, according to recent compensation data. For mid-sized organizations, that expense can consume a significant portion of the annual IT budget. It leaves little room for other critical security investments such as cloud security, monitoring tools, and employee security training.
A vCISO provides comparable leadership for a fraction of that cost.
Typical vCISO engagements range from $5,000 to $20,000 per month, depending on scope and company size, which equates to roughly $60 K to $240 K annually.
According to industry research, vCISO services cost 30% to 70% less than full-time CISO hires. This allows growing businesses to redirect those savings into risk management tools, cloud security improvements, and security awareness training while still benefiting from executive-level cybersecurity leadership.
Recruiting a permanent CISO can take months, and turnover is high. And when that leader leaves, you face another expensive search and months without direction.
On the other hand, a vCISO offers stability through a service model where another qualified expert can step in immediately to maintain oversight of cybersecurity strategy, compliance requirements, and security controls.
Why “Partial” Leadership Can Deliver Full-Scale Value
Some executives assume a part-time leader cannot have the same impact as someone in the office every day. In practice, vCISOs focus on high-impact strategic work rather than routine IT tasks. They evaluate your organization’s security posture, define measurable goals, and align the cybersecurity roadmap with business priorities.
A vCISO may spend a few focused hours each week reviewing incident reports, advising on security policies, and briefing executives on progress. That concentrated attention produces measurable improvements faster than a full-time role distracted by operational details.
Another major advantage of the vCISO model is access to specialized cybersecurity expertise. Most fractional CISOs belong to networks that include experts in areas such as compliance audits, regulatory frameworks, and cloud security.
When a project demands niche knowledge, such as building a vendor-risk program or mapping a cybersecurity framework, the vCISO can draw on those additional resources without adding permanent staff.
Sign 2: Your Internal Team Lacks Cybersecurity Depth or Direction
Many mid-sized companies assume their IT department has security covered. In reality, most internal teams are focused on daily operations, help-desk requests, and infrastructure maintenance, so cybersecurity is handled informally at best.
When no one owns information security strategy, critical functions such as risk management, compliance audits, and incident response are often incomplete or missing entirely. This lack of leadership is a clear sign that a vCISO could help.
Gaps in Security Strategy and Oversight
IT professionals are capable and hardworking, but they are not always cybersecurity specialists. Their attention is divided between routine issues and reactive fixes. Without a defined cybersecurity strategy, essential questions go unanswered. What are the organization’s biggest threats? Is there a security roadmap or incident response plan?
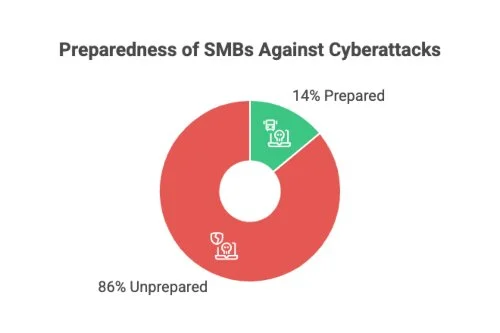
The statistics highlight the issue. 43% of all cyberattacks target small and mid-sized businesses. However, only 14% feel ready to defend themselves.
This mismatch shows how much risk exists when security programs depend on overextended IT staff. Even more concerning, less than 30% of SMBs manage cybersecurity in-house in a dedicated way. Most rely on managed service providers or ad hoc tools, leaving major gaps in security controls and reporting.
A vCISO brings the structure and accountability missing in these scenarios. They assess your current cybersecurity posture, identify weaknesses, and create a governance model that aligns with business goals and regulatory requirements. By introducing formal risk management and consistent reporting, they ensure that cybersecurity becomes measurable, proactive, and tied to business outcomes.
The Role of a vCISO as a Strategic Partner
A vCISO functions as both mentor and strategist for your internal team. They start with a risk assessment to establish a baseline of security maturity, then build a roadmap with clear milestones and owners. This might include implementing multi-factor authentication, improving cloud security, or preparing for compliance audits.
Equally important, the vCISO invests in developing internal talent. They lead workshops, guide vulnerability management, and introduce repeatable processes that improve confidence and skill across the IT department. Over time, your internal staff gains the cybersecurity expertise needed to sustain improvements.
Finally, a vCISO acts as the translator between technical teams and business leaders. They present risks and solutions in business terms, helping executives understand why certain security investments are necessary.
This communication ensures that leadership approves the resources and policies required to strengthen your overall security posture. With a vCISO guiding strategy, your IT team can focus on execution while the organization gains direction, maturity, and resilience.
Sign 3: You’re Struggling with Regulatory or Industry Compliance
For many organizations, the wake-up call that they need cybersecurity leadership comes from compliance requirements. Maybe a client asks about SOC 2 certification or a new privacy law like GDPR adds obligations that your team does not fully understand.
Industries such as healthcare, finance, and defense must also meet strict standards like HIPAA, PCI-DSS, NIST, or CMMC. When navigating these frameworks starts to feel overwhelming, a vCISO can help simplify and manage the process.
Expanding Cyber Requirements Across Sectors
Regulatory expectations now reach businesses of every size. Enterprise clients often require proof of cybersecurity readiness before signing contracts, and smaller vendors are expected to comply with their partners’ standards.
Healthcare providers must protect data under HIPAA, retailers must meet PCI-DSS for payment processing, and technology companies often need SOC 2 or ISO 27001 certifications to maintain trust.
In fact, 79% of SMBs cite compliance as a top cybersecurity challenge. Requirements evolve quickly, and what was optional last year may be mandatory today.
Many firms find themselves reacting to changes instead of planning for them, often wasting money on unnecessary controls or missing essential ones. When your team is unsure how to interpret compliance language or prepare for audits, that is a strong indicator that expert guidance is needed.
How a vCISO Bridges Policy and Practice
A vCISO understands how to translate regulations into clear, achievable actions. They start with a gap analysis comparing your existing security posture to required standards.
For example, if you are pursuing SOC 2, the vCISO will assess access controls, incident response, and change management, then build a prioritized remediation plan. They also write or update key policies such as acceptable use, data classification, and vendor risk management.
Beyond documentation, a vCISO turns compliance into a living process. They establish internal audits, schedule regular control reviews, and train staff so compliance becomes part of daily operations rather than a once-a-year rush.
For organizations facing multiple frameworks, a vCISO creates a unified control set that satisfies overlapping requirements like NIST, ISO 27001, and HIPAA. This approach prevents duplication and reduces compliance fatigue.
Risk of Noncompliance
Regulatory noncompliance now carries a measurable financial penalty when a breach occurs. Data breaches involving regulatory noncompliance cost organizations an average of $4.61 million, which is 4% higher than the global average breach cost. In addition, breaches in which noncompliance was identified as a contributing factor cost nearly $174,000 more on average than those without compliance failures.
These findings show that even minor lapses in regulatory readiness, such as incomplete documentation or missing controls, can significantly increase the financial impact of a cyber incident.
A vCISO helps prevent these outcomes by integrating compliance into everyday operations. They develop policies, perform regular gap assessments, and ensure your organization can demonstrate accountability to regulators, clients, and partners. With the right oversight, compliance becomes a foundation for resilience and trust rather than a costly afterthought.
Sign 4: Your Business Is Growing Faster Than Your Security Maturity
Growth is good for business until security starts to lag behind. If your company is scaling quickly by hiring, expanding into the cloud, or acquiring other organizations, there is a real risk that security governance is not keeping pace.
Many firms double in size yet rely on the same security policies, tools, and staffing as before. When complexity expands faster than security maturity, a vCISO can restore balance.
The Security Lag Problem
Rapid expansion exposes weaknesses that were previously hidden. You might migrate workloads to the cloud but overlook identity management, access provisioning, or misconfiguration risks.
You may have more employees, remote users, and SaaS platforms but no unified policy for password management or device security. Mostly the result is inconsistent standards, unmanaged assets, and data exposure.
By 2024, 63% of small and mid-sized business workloads were hosted in the cloud. This shows how widespread cloud adoption has become. Yet many companies still lack a defined cloud security framework. In mergers or acquisitions, systems and data from acquired entities may remain outside your centralized controls.
Each of these changes expands the attack surface while leaving critical vulnerabilities unaddressed.
Scaling Security Proportionally
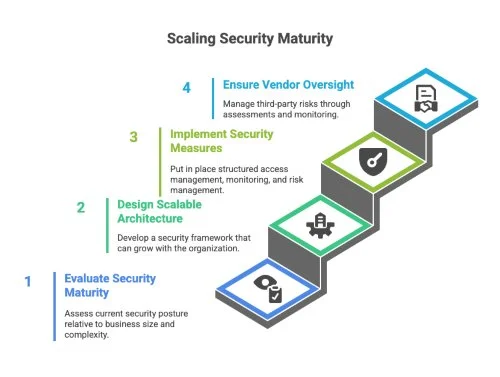
A vCISO evaluates your security maturity relative to business size and operational complexity. When you were a 50-person organization, basic antivirus and a single firewall may have sufficed. At 200 employees with multiple locations and SaaS applications, you need structured access management, centralized monitoring, and a formal risk management program.
The vCISO identifies what needs to evolve and helps design a roadmap for implementation.
They create a scalable architecture with clear baselines. Every new application, system, or acquisition undergoes a security review. All new offices follow standard configurations, and vendor security assessments become part of procurement. The vCISO also drives consistency by unifying policies and tools across departments so that no business unit operates in isolation.
Vendor oversight becomes critical as your network of suppliers grows. A vCISO implements a third-party risk management program that evaluates vendor security posture, establishes contractual requirements, and ensures ongoing monitoring. This approach prevents supply-chain vulnerabilities that can compromise the entire organization.
Aligning Security with Business Growth
A vCISO ensures your cybersecurity strategy grows in step with business goals. Entering new markets or launching new services introduces regulatory and security challenges.
For example, expanding into Europe creates GDPR obligations, while offering healthcare-related services triggers HIPAA requirements. The vCISO plans for these early, helping you remain compliant while pursuing expansion.
They also integrate security into innovation and technology projects. Whether implementing new customer platforms or cloud solutions, the vCISO ensures security is embedded from the beginning rather than patched in later. This reduces future costs, protects data, and supports sustainable growth.
Sign 5: You’ve Experienced (or Fear) a Breach or Major Incident
For many organizations, the need for cybersecurity leadership becomes clear only after a breach, ransomware attack, or serious close call.
Even if your company has avoided a major incident, the constant worry that “it’s only a matter of time” is a sign of risk. If you are unsure your current team can handle a targeted attack, a vCISO can turn a reactive posture into a proactive strategy.
Moving from Reactive to Proactive Security
After an incident, most companies realize their approach was reactive rather than preventive. The cost of late response is enormous.
Average downtime from a cyberattack costs about $53,000 per hour when lost revenue and recovery efforts are included. No surprise that 78% of SMB leaders fear a major breach could shut them down.
A vCISO helps stop this cycle. They begin with a root-cause analysis to understand what went wrong and which vulnerabilities were exploited. They then design preventive controls and update security policies to close those gaps.
Many organizations lack an incident response plan altogether. Studies show 47% of small businesses have no documented incident response plan. This leaves them unprepared for even minor disruptions.
How a vCISO Builds a Resilient Incident Response Plan
Developing an incident response plan is one of the first tasks a vCISO tackles. The plan defines who leads during an event, who communicates with legal and PR, and what steps to take in scenarios such as ransomware, data theft, or insider misuse.
The vCISO then runs tabletop exercises, where executives and staff practice simulated breaches to test readiness and coordination. These drills identify weaknesses in communication and process before a real crisis occurs.
A vCISO also improves early threat detection and monitoring. They can deploy intrusion detection systems, implement continuous log analysis, or partner with managed security operations centers to watch for anomalies around the clock. They may also add industry-specific threat intelligence to help you anticipate attacks rather than react to them.
Human error is another key vulnerability. A vCISO establishes ongoing security awareness training that includes phishing simulations and regular refreshers. When an incident happens, they lead post-incident reviews and update policies based on lessons learned. Over time, this builds a confident, resilient security culture rather than one driven by fear.
Insurance and Client Confidence Impacts
A mature incident response program directly affects your ability to get and maintain cyber insurance. Only 17% of small businesses carry cyber insurance, and insurers now require evidence of controls such as multi-factor authentication and regular backups. A vCISO ensures your organization meets these standards, helping secure coverage at reasonable rates.
A vCISO also helps strengthen client trust. When customers ask about your incident response readiness, you can confidently point to your formal plan, leadership oversight, and training schedule.
This credibility can make the difference between keeping or losing a major account after a breach. With a vCISO guiding your strategy, you not only reduce the likelihood of incidents but also minimize financial and reputational fallout when they occur.
Sign 6: Clients, Partners, or Insurers Demand Stronger Security
Sometimes the pressure to strengthen cybersecurity comes from outside your organization. Customers, business partners, and insurers increasingly expect proof of strong controls before they sign contracts or renew policies.
If you are struggling to meet these external expectations, a vCISO can help you meet requirements while turning security into a competitive advantage.
External Pressures Are Now Business-Critical
Enterprise clients increasingly require detailed vendor security questionnaires before approving new partnerships. These assessments often include hundreds of questions about encryption practices, access controls, and risk management procedures.
Companies that cannot respond with clarity and documented evidence of their security posture risk losing valuable contracts or delaying onboarding. Business partners also expect alignment with established frameworks such as SOC 2, ISO 27001, or NIST to ensure shared trust and reduce overall third-party risk.
Cyber insurers have followed suit. Insurance applications now request documentation of incident response plans, security training, and technical safeguards. Premiums have increased for those without mature programs, with some reports showing cyber insurance premiums up more than 30% year over year.
Incomplete security practices can even lead to denied claims after an incident, as insurers verify that stated controls are truly in place. These external pressures have made cybersecurity leadership an operational necessity rather than a luxury.
Lost opportunities are another consequence. Maybe a potential client backed out because you lacked a SOC 2 report, or your engineers spend days completing technical assessments instead of product work. These situations highlight the need for a structured, repeatable process that a vCISO can build and manage.
Strengthening Reputation and Competitive Edge
Engaging a vCISO is not only about satisfying outside requirements. It also helps position your organization as a trusted, mature partner. A vCISO can lead efforts to earn certifications or compliance attestations such as SOC 2 or ISO 27001. These credentials demonstrate that your company manages information security systematically, often accelerating enterprise sales and partnership approvals.
Even without certification, a vCISO can create a Trust Center summarizing your cybersecurity framework, governance, and incident readiness. Having a designated vCISO signals that your organization takes data protection seriously.
A vCISO also ensures you meet insurer expectations by implementing baseline security controls such as multi-factor authentication, regular backups, and incident response testing. These improvements not only enhance resilience but also help secure better insurance terms.
Strong cybersecurity can ultimately become a competitive differentiator. When two suppliers offer similar value, the one with visible, verifiable security leadership will win. By investing in a vCISO, your company gains credibility, satisfies external demands, and builds long-term trust across clients, partners, and insurers.
The True Cost of Delay: Why Waiting to Hire a vCISO Is Risky
Some businesses recognize they need cybersecurity leadership but still hesitate, hoping to manage a little longer without it. The reality is that delaying action increases both financial and reputational risk.
Each month without structured oversight allows vulnerabilities to grow while opportunities are lost. Waiting for a breach to justify investment often turns into the costliest decision a company can make.
Financial and Reputational Fallout
Cyber incidents grow more severe when security programs remain immature. A small issue that could have been prevented or contained early can escalate into a business-ending event. Studies show 60% of small businesses close within 6 months of being breached.
The reputational cost can be just as damaging. 36% of small and mid-sized firms lose customers after a cyber incident, whereas 12% have to face legal trouble. In addition to this, many face contract cancellations or reduced market trust.
Rebuilding credibility requires significant time and marketing expense. On top of that, fines and settlements for compliance failures are often higher than the cost of prevention.
A vCISO prevents these outcomes by implementing strong governance, security controls, and incident response plans before a crisis occurs. It is the difference between having a fire prevention system and waiting until the flames spread. Acting early minimizes both the likelihood and the impact of future incidents.
Missed Opportunities for Risk Reduction and Growth
Waiting to hire a vCISO also means losing the business advantages that come with security maturity. Companies without leadership often delay pursuing enterprise clients, certifications, or new markets because they are not audit-ready.
A vCISO can help achieve compliance milestones such as SOC 2 or ISO 27001 within months, enabling access to higher-value contracts and regulated industries.
Internally, the longer an organization operates without expert guidance, the more security debt accumulates. Outdated systems, inconsistent configurations, and missing documentation take much longer to correct later. A vCISO provides a structured plan to resolve these issues gradually and sustainably, avoiding rushed, expensive overhauls after a breach or audit failure.
Cybersecurity maturity also supports long-term business goals. Investors and acquirers now evaluate information security during due diligence. A company with CISO-level leadership, established security controls, and compliance readiness signals lower risk and higher operational discipline. Delaying this investment can reduce valuation or disqualify you from key opportunities.
Partner with AAG for Expert vCISO and Cybersecurity Leadership
Cybersecurity leadership is no longer optional for growing organizations.
Whether your challenges involve compliance, scaling, or recovering from a breach, having the right expertise at the executive level is what separates proactive companies from reactive ones.
A Virtual or Fractional CISO brings the strategy, structure, and accountability needed to protect both your business and your reputation.
If you’re ready to strengthen your security program and build lasting resilience, contact Alpha Apex Group to learn how our vCISO and fractional cybersecurity leadership services can help guide your next stage of growth with confidence.
Frequently Asked Questions
What is the 80/20 rule in cybersecurity?
The 80/20 rule suggests that 80% of security risks can often be reduced by addressing the most critical 20% of security controls. This approach focuses on high-impact measures such as patch management, access control, and employee training before moving to lower-priority issues.
What size company needs a vCISO?
A vCISO is a strong fit for small and mid-sized businesses that need executive-level cybersecurity guidance but do not require or cannot afford a full-time CISO. These companies typically face growing compliance demands and complex risks while needing flexible, scalable support.
What are the 7 types of cybersecurity?
The seven key types include network security, cloud security, endpoint security, application security, data security, identity and access management, and operational or infrastructure security. Each area plays a specific role in protecting systems, data, and users across the organization.
Can AI replace a vCISO?
AI can improve cybersecurity by automating detection and analysis, but it cannot replace the strategic leadership of a vCISO. Human expertise is still essential for interpreting risk, setting policy, and aligning security programs with business objectives.