Top 10 Virtual CISO Consulting Services
In a world where cyber threats keep growing more complex, companies need strategic leadership in cybersecurity. For many organizations, hiring a full‑time CISO is expensive, slow, or unscalable. That’s where Virtual CISO (vCISO) consulting steps in to offer expert risk assessments, compliance strategy, security roadmap creation, and executive‑level guidance without the overhead of a full permanent hire.
Here’s what the latest research tells us:
The global average cost of a data breach jumped to US$4.88 million in 2024, a 10% increase from 2023, driven largely by business disruption, customer remediation, and regulatory costs
vCISO services are exploding in adoption: the share of managed service providers (MSPs/MSSPs) offering vCISO went from 21% in 2024 to 67% in 2025, a more than 300% year‑over‑year increase
Automation and AI are supercharging efficiency: among providers using vCISO services, 81% already use AI or automation, and those tools are delivering up to a 68% drop in workload related to reporting, risk assessments, and compliance tasks
These numbers add up to a clear signal: strategic cybersecurity advice (not just tools or reactive fixes) is now a top priority.
If risk assessments, compliance, and security roadmaps aren’t part of your game plan, your company is leaving too much on the table and risking financial exposure, regulatory risk, and gaps in resilience.
This article shows you the top virtual CISO consulting services that can help you tackle those problems, but first:
What Is a Virtual CISO Consulting Service?
A Virtual Chief Information Security Officer (vCISO) consulting service gives your organization access to senior-level cybersecurity leadership without the full-time cost or overhead of hiring an in-house CISO.
Instead of one executive on payroll, you tap into a consulting partner (or team of seasoned professionals) who provides the same strategic direction, governance expertise, and risk management oversight as a permanent CISO.
At its core, a vCISO consulting service is about strategy and alignment. These consultants work directly with your leadership team to:
Build a security roadmap tied to your business objectives
Identify, prioritize, and mitigate cyber risks
Make sure you comply with relevant regulations and client demands
Guide incident response planning and crisis management
Translate complex technical risks into clear, board-ready insights
Unlike traditional “managed services” that focus only on operational tasks (like monitoring or patching), a vCISO consulting engagement is advisory-heavy and executive-focused. That means you’re bringing in trusted advisors who know how to balance protection, compliance, and business growth.
Done right, this leads to a stronger security posture, a clear strategy your executives can act on, and the confidence that your organization is making smart, risk-informed decisions.
Benefits of Working with a Virtual CISO Consulting Service
Hiring a full-time Chief Information Security Officer can easily cost six figures a year, and that’s before bonuses, benefits, and the team they’ll need to be effective. For many organizations, it’s simply not practical. That’s where a virtual CISO consulting service comes in. They can give you the same caliber of leadership and strategy, without the overhead or long-term commitment.
Here are the biggest advantages decision-makers can expect:
Board-level security leadership without the price tag
A vCISO consulting service ensures you get executive-level leadership without the overhead of a full-time hire. Instead of recruiting, vetting, and paying a six-figure executive plus benefits, you can engage a consulting partner who provides ready-to-go leadership on a flexible basis.
Alpha Apex Group backs this with an 80% placement success rate and an average of 43 days to fill leadership roles, giving clients rapid access to proven security leadership.
Compliance without the headaches
A consulting service gives you access to vCISOs who already have experience running HIPAA, CI-DSS, and SOC 2 programs across industries. Instead of testing one hire’s limited background, a service connects you with specialists matched to your regulatory environment and swaps them if your needs evolve.
At Alpha Apex Group, we also run proprietary audits to flag compliance gaps early, so you walk into board reviews and regulatory exams with confidence.
Faster, smarter risk management
A consulting service accelerates the vCISO hiring process by maintaining a roster of vCISOs with proven playbooks for risk identification and mitigation.
You don’t waste months onboarding an executive who needs to learn from scratch. You get someone who’s done it before, in your industry. With CVs delivered in as little as 72 hours and a 90-day replacement guarantee, Alpha Apex ensures risk management leadership is never left vacant
Scalable expertise that grows with you
A consulting service scales with your business. Whether you need part-time advisory support, full program build-outs, or interim leadership after turnover, the consulting model adjusts without the long-term salary burden.
Alpha Apex Group’s proprietary dashboard processes 400+ daily inquiries from security professionals, giving you access to scalable expertise as your needs change.
Independent perspective you can trust
Internal teams can miss blind spots. A vCISO consultant brings an outside view, challenging assumptions, testing resilience, and making sure your leadership has the full picture before making decisions.
Alpha Apex Group reinforces this independence with in-house thought leadership research, so companies like yours benefit from collective intelligence and industry benchmarks.
Proven playbooks, tailored to you
A consulting service matches you with vCISOs who already have playbooks tailored to organizations like yours. Instead of reinventing the wheel with a single hire, you get access to field-tested frameworks (NIST, ISO, CIS) combined with service-level customization.
That consulting-layer oversight ensures consistent quality across engagements.
TL;DR Top 5 Virtual CISO Consulting Services
Alpha Apex Group: Alpha Apex Group delivers board-level security leadership through flexible vCISO consulting and recruiting, with 80% placement success, 43-day average fills, 72-hour CV delivery, proprietary audits, and scalable, compliance-ready expertise.
RSI Security: RSI Security blends board-level strategy with hands-on execution and AI-driven efficiency to give you scalable security leadership at a fraction of the cost of a full-time CISO.
ProCircular: ProCircular delivers modular vCISO services, whether you need a full partner, interim leadership, or extra bandwidth, so you always get the right level of security guidance for your stage of growth.
PurpleSec: PurpleSec gives startups and SMBs flexible, risk-based vCISO leadership that prioritizes high-impact actions.
FRSecure: FRSecure provides vendor-neutral, security-only leadership, so every recommendation strengthens your program.
Top 10 Virtual CISO Consulting Services
The best virtual CISO consulting services include Alpha Apex Group, RSI Security, PurpleSec, Pro Circular, and more. In this section below, we’ll explain how they operate and what benefits they bring.
1. Alpha Apex Group
Alpha Apex Group is an executive recruiting partner specializing in CISO, vCISO, and technology leadership roles. We don’t deliver vCISO services ourselves; instead, we connect you with the right leaders who do.
Whether you’re facing a cybersecurity leadership gap, preparing for a digital transformation, or need stability during a high-stakes exit or funding round, we bring in the right executive.
Unlike firms that offer generic interim staffing, we tailor each placement to your business’s current state and future trajectory. We start by helping you define exactly what kind of leader you need by looking at scope, mandate, and outcomes. From there, we match you with executive-level talent who’ve led similar initiatives in comparable industries.
Our engagements are flexible, outcomes-driven, and structured around your priorities, from stabilizing risk to launching long-term security programs. For organizations that can’t afford a six-month hiring cycle or a misaligned executive, our model saves time, reduces risk, and delivers traction where it matters.
We combine speed with precision: CVs are in your inbox within 72 hours, we average just 43 days to fill leadership roles, and we deliver an 80% placement success rate. Every engagement includes a 90-day replacement guarantee to minimize risk. Behind the scenes, our proprietary dashboard processes 400+ candidate inquiries daily, giving us a constantly refreshed pipeline of security, technology, and operations leaders.
Our bench spans roles like CISO, CTO, CIO, and COO across sectors, including healthcare, life sciences, tech, energy, and regulated industries. And these are all sectors where leadership missteps carry high regulatory or financial costs.
Alongside recruitment, we provide in-house thought leadership research and proprietary audits that help you see around corners and align leadership with compliance, investor expectations, and long-term growth goals. Our executive partners drive real change, enforce accountability, and leave behind systems that keep working long after we’ve moved on.
Key Services
Strategic placement of fractional and interim CISOs and other C-suite leaders
Engagement scoping and mandate definition aligned to business goals
Outcome-based or incentive-aligned compensation models
Deep industry matching across regulated and innovation-driven sectors
Advisory integration to ensure traction beyond the interim period
Why work with Alpha Apex Group?
Because they take extensive steps to find leaders who are handpicked to drive your next big move, based on your specific strategy, risks, and constraints.
2. RSI Security
RSI Security provides virtual CISO (vCISO) services for companies that want senior‑level cybersecurity leadership without hiring a full‑time CISO.
They help their clients define and drive long‑term strategy (risk posture, governance, compliance) while also setting up the practical programs needed to execute. They customize their approach depending on your organizational maturity and adjust their level of involvement as your risk profile or compliance demands change.
RSI’s vCISO team does things like: perform detailed risk gap assessments, establish information security roadmaps, design and enforce security policies, lead incident response plan design (and execution if needed), implement security awareness programs for staff, and support regulatory or audit compliance requirements.
They also lean on automation tools (AI/ML) to make governance and monitoring more efficient. For example, they use AI‑assisted vCISO features to automate threat monitoring, risk assessment workflows, and to streamline compliance tasks.
They’re especially useful for small‑to‑medium organizations that need both interim guidance (plugging gaps or responding to threats) and a solid, strategic program to work toward long‑term security maturity.
Key Services Provided by RSI Security (vCISO Related)
Cybersecurity strategy definition & road‑mapping
Risk assessments, gap analysis, vulnerability scanning
Governance, compliance & policy creation (audit readiness, regulatory frameworks)
Incident response planning & execution support
Security awareness programs & staff training
Access management and monitoring (privileged access, least privilege, etc.)
AI/ML‑assisted automation for monitoring, risk reporting, and compliance workflows
Why work with RSI Security?
Because they combine strong strategic vision with hands‑on execution, and offer AI‑driven efficiencies that let you get high‑level cybersecurity leadership at lower cost.
3. ProCircular
ProCircular delivers virtual CISO services designed to align security, risk, compliance, and privacy with what your business is actually trying to do.
They’re not “one‑size‑fits‑all”: depending on where you are in maturity, what your threat landscape looks like, or how tight your budget is, ProCircular can:
Act as your full CISO
Serve in a transitional/interim capacity
Or supplement an existing internal security leadership team
They help with everything from designing a security roadmap to implementing key programs (policy, risk assessment, incident response, awareness, etc.) and maintaining oversight.
ProCircular works across industries like finance, healthcare, education, government, manufacturing, defense contracting, and transportation. Because of that spread, they bring both regulatory experience (for regulated sectors) and pragmatic hands‑on execution (for more fast‑paced, less regulated ones).
They also offer more than just advice: you get subject matter experts, real prioritization of what to execute first, and ongoing coordination/oversight rather than a “hand off and let’s hope” model.
Key Services
Full Partner vCISO service (ProCircular acts as your de facto CISO for the duration of the engagement)
Transitional / Interim vCISO: covering gaps while permanent leadership is hired or during big transitions
Supplemental vCISO: improving or supporting an existing security team or internal CISO, adding bandwidth or expertise as needed
Security strategy & roadmap design to fit your business goals
Hands‑on implementation assistance & execution oversight of policy, incident response, and risk/compliance programs
Governance, Risk & Compliance consulting (regulatory mapping, compliance readiness)
Security awareness training, tabletop incident exercises, and continuous monitoring tools/services
Why work with ProCircular?
Because ProCircular offers modular executive leadership, you’re not locked into a full vCISO program when you only need targeted strategic support. Whether you're filling a short-term leadership gap or augmenting an existing team, they adapt the model to your stage of maturity.
4. PurpleSec
PurpleSec offers virtual CISO services built to give smaller organizations like startups and SMBs executive‑level cybersecurity leadership without the high cost or commitment of a full‑time CISO.
Their process is phased: first, a full assessment of your current security posture (tech, policies, risks), then a tailored strategic roadmap aligned with your business goals, and finally implementation of prioritized security projects.
Common deliverables are policy and architecture reviews, risk and vendor risk assessments, incident response planning, data classification, audit readiness, identity and access management, and vulnerability remediation. Because they focus on lean organizations, they emphasize risk‑based prioritization so that every dollar and hour invested has high impact.
They’re especially strong for companies that need to move quickly: PurpleSec gives you the ability to engage on demand, flexibly scaling up or down depending on what issues come up.
Key Services PurpleSec Provides
Security posture assessments (documentation, technologies/policies) and maturity benchmarking
Risk assessments: internal, external, vendor risk, data classification
Strategy and roadmap design (often 2‑3 year plans), prioritizing high‑impact areas
Policy development and security architecture review
Incident response planning (and oversight of readiness)
Ongoing tasks: vulnerability management, identity and access management, audit/compliance readiness
Flexible engagement/pricing models: monthly retainer, hourly, or project-based
Why work with PurpleSec?
PurpleSec’s USP is high‑impact leadership when you need it most: you get expert CISO‑level guidance priced and scoped for organizations that don’t have huge security budgets and can’t afford long delays.
5. FRSecure
FRSecure’s approach to vCISO services is intentionally flexible: they meet you where you are in terms of security maturity, map out realistic improvements, and then help you implement them in a way that makes sense within your specific business objectives.
Engagements start with a thorough onboarding process and a full risk assessment that covers administrative, physical, and technical vulnerabilities. From there, FRSecure builds a prioritized security roadmap focused on the most pressing gaps and the improvements that will have the biggest measurable impact. Once the plan is in place, their vCISO stays engaged for the long term and provides hands-on leadership for policy development, compliance management, employee awareness training, and executive-level reporting.
Unlike firms that bundle vCISO services into broader IT offerings, FRSecure focuses purely on information security. That means the guidance you get is specialized and unbiased, and built to strengthen your security program rather than push products.
And as your program matures, engagements naturally become more cost-efficient as they shift to long-term monitoring and coaching.
Key Services
Comprehensive risk and vulnerability assessments
Security roadmap creation tailored to business goals and maturity
Ongoing vCISO engagement for policy, process, and compliance oversight
Incident response planning and tabletop exercises
Employee training and awareness programs
Asset management and continuous monitoring
Executive and board presentations to align stakeholders
Why work with FRSecure?
Because FRSecure is one of the few firms that offer dedicated, vendor-neutral security leadership, which gives your organization the expertise and strategic roadmap it needs without distractions from hardware sales or one-size-fits-all IT bundles.
6. Happiest Minds
Happiest Minds provides virtual CISO services designed for enterprises that need senior cybersecurity leadership without the overhead of a full-time executive. Their service range is built around solving common enterprise challenges like evolving threats, cloud and IoT sprawl, compliance demands (like ISO-27001, PCI-DSS, NIST), skills shortages, limited budgets, and slow incident response times.
Instead of providing a single advisor, Happiest Minds frames its vCISO service as a set of specialized leadership roles so the engagement matches your organization’s stage and pain points.
At the strategic level, their vCISOs help align cybersecurity with your business objectives by tying security into culture, policies, and day-to-day processes.
On the operational side, they guide incident response, disaster recovery, risk governance, and audit readiness. They also act as a liaison with regulators and assessors, which gives organizations a smoother path through certifications and compliance reviews.
Key Services
Strategic cybersecurity leadership aligned to business goals
Risk governance, incident response, and disaster recovery planning
Security program design & integration into business processes and culture
Advisory and training support for leadership and staff
Regulatory and compliance support (ISO-27001, PCI-DSS, HIPAA, NIST, etc.)
Threat and vulnerability assessments across cloud, IoT, and hybrid environments
Why work with Happiest Minds?
Because they provide a multirole vCISO framework (Strategist, Advisor, Guardian, Technologist), which gives enterprises leadership that covers the boardroom as well as the technical needs, depending on where your biggest risks lie.
7. Kroll
Kroll’s model is built around embedding senior security expertise, delivered by former CISOs with boardroom and regulatory experience, into companies that need both immediate stabilization and long-term program maturity.
Engagements typically start with an in-depth assessment of an organization’s culture, policies, and technical posture.
From there, Kroll builds a roadmap using established frameworks such as NIST SP 800-53 and aligns it with specific regulatory demands like PCI-DSS, HIPAA, or GDPR.
Unlike firms that stop at recommendations, Kroll supports remediation and policy development by working with technical teams to harden environments while giving executives and boards the visibility they need to make informed decisions.
For leadership teams under pressure, Kroll offers something particularly valuable: translation. Their vCISOs bridge technical and business language, which means conversations about risk land with clarity and accountability at the board level. This makes them a strong fit for organizations that deal with complex compliance obligations or heightened stakeholder scrutiny.
Key Services
Security strategy development mapped to frameworks (NIST, ISO, CIS) and regulations (PCI, HIPAA, GDPR, etc.)
Risk and vulnerability assessments, including third-party risk management
Policy and procedure development, with hands-on remediation support
Executive and board reporting to improve visibility and accountability
Security awareness training and phishing simulations
Environment and network hardening for stronger baseline resilience
Why work with Kroll?
Because their vCISOs combine technical depth with board-level communication, which helps organizations close gaps faster while earning executive and regulatory confidence.
8. Defensible Technology
Defensible Technology delivers its vCISO+ service as a way for organizations to gain executive-level security leadership with the advantage of pre-tested frameworks and actionable execution support.
Rather than starting from scratch, clients benefit from a hybrid model: seasoned CISOs who bring risk-based judgment and business alignment, combined with a library of field-tested policies and program templates that speed up progress. This approach is especially valuable for organizations that need to advance their security maturity quickly.
The vCISO+ service is designed to integrate directly into business processes so security priorities are communicated clearly to leadership and acted on consistently across teams.
Whether it’s drafting policies aligned with industry standards, building disaster recovery playbooks, or simulating incident response with tabletop exercises, Defensible bridges the gap between strategy and day-to-day execution. The result: organizations can set a direction, and more importantly, get the tools and processes to stay on track.
Key Services
Policy and standards development aligned with regulatory frameworks
Incident response planning and tabletop simulation exercises
Business continuity and disaster recovery planning
Security awareness training for staff across all levels
Roadmap and budget planning to prioritize initiatives with clear ROI
Governance, KPIs, and reporting to leadership with actionable insights
Why work with Defensible Technology?
Because they deliver proven, reusable playbooks combined with custom leadership to help organizations mature faster and with fewer false starts.
9. Pivot Point Security
Pivot Point Security provides virtual CISO leadership designed around compliance-heavy environments. Their vCISO service is built to help organizations meet and prove adherence to demanding frameworks like ISO 27001, SOC 2, FedRAMP, HITRUST, and CMMC. That’s critical in industries where client trust and contractual obligations hinge on certification and audit readiness.
The service follows a structured model, much like all consulting services in this review. They begin with a gap analysis, build both a long-term roadmap and a near-term action plan, then continuously monitor and adjust as threats and regulations evolve.
Along the way, they integrate vendor risk management, incident response preparedness, and governance design so that security becomes sustainable instead of just a one-time effort. By combining risk-based strategy with compliance execution, Pivot Point helps organizations close audit gaps while also building resilience against real-world threats.
Key Services
Security risk assessments and roadmap development
Compliance and audit preparation (ISO 27001/27701/42001, SOC 2, FedRAMP, HITRUST, CMMC)
Threat intelligence and continuous monitoring
Policy and governance development aligned with NIST, ISO, and other standards
Third-party vendor risk assessments and management
Incident response planning, testing, and readiness
Why work with Pivot Point Security?
Because they bring compliance-first security leadership, which is ideal for organizations where proving adherence to frameworks is just as important as reducing risk.
10. Centric Consulting
Centric Consulting offers fractional and interim vCISO services designed to give organizations senior security leadership without the commitment of a full-time executive. Their model is highly flexible and can be part-time, project-based, or interim, depending on what your organization needs most.
This adaptability makes them a strong choice for companies dealing with transitions or facing compliance deadlines.
Centric Consulting starts by advising boards and leadership teams on translating cyber risk into business terms, setting strategy, and building actionable roadmaps. From there, they help organizations strengthen governance, risk, and compliance programs. They can improve resilience through incident response planning and execute security projects with speed and focus.
Key Services
Executive advisory and board-level cybersecurity strategy
Governance, risk, and compliance (GRC) framework development
Threat monitoring, incident response, and resilience planning
Identity and access management plus internal audit support
Security project management and remediation execution
Risk quantification and integration with business objectives
Why work with Centric Consulting?
Because their USP is adaptability with executive depth, you get seasoned security leadership that’s matched precisely to your needs, whether that’s three months of audit prep, ongoing board-level guidance, or a steady hand during leadership transitions.
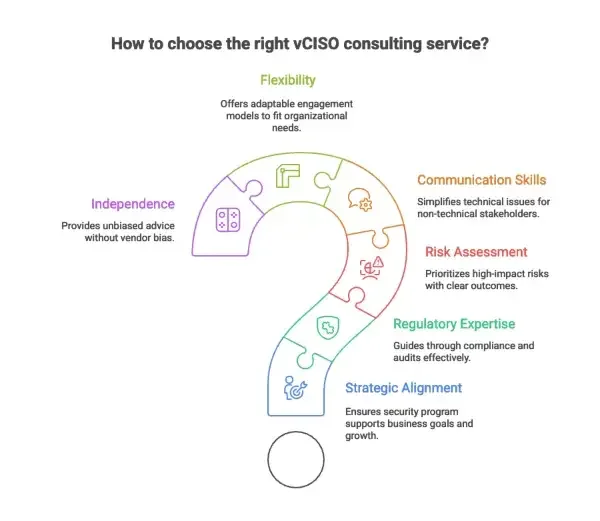
How to Choose the Right Virtual CISO Consulting Service
Not every vCISO consulting service is created equal. For decision-makers, the right choice comes down to finding a partner who can provide strategic security leadership while fitting seamlessly into your organization’s goals, risk profile, and culture.
Here are the key factors to evaluate, plus the red flags and questions you should raise during the selection process.
1. Strategic alignment with business goals
A strong vCISO doesn’t just manage firewalls and policies; they help shape your security program around business growth, compliance, and client trust. Look for providers who can talk fluently about risk in financial and operational terms.
Red flag: They focus too heavily on tools or technology stacks without connecting security back to revenue, compliance, or customer trust.
Ask: “How do you translate cyber risk into business metrics for executives and the board?”
2. Depth of regulatory and framework expertise
From GDPR and HIPAA to SOC 2 and CMMC, compliance is a lot of times the driver behind bringing in a vCISO. You need a partner who knows the frameworks and can guide you through audits.
Red flag: Overreliance on one framework (e.g., NIST CSF only) without tailoring to your industry’s unique obligations.
Ask: “Which regulatory frameworks do you most often guide clients through, and how do you adapt them to different industries?”
3. Risk assessment and prioritization capabilities
Good vCISO services focus on the highest-impact risks first. The right partner should provide structured assessments, risk quantification, and a clear roadmap.
Red flag: They deliver laundry-list audits with no prioritization or measurable outcomes.
Ask: “How do you decide which risks to address first, and how do you measure progress over time?”
4. Communication and executive presence
Your vCISO should be comfortable briefing boards, coaching executives, and simplifying technical issues for non-technical stakeholders. Leadership presence matters as much as technical knowledge.
Red flag: They overcomplicate issues with technical detail or can’t confidently present at the executive level.
Ask: “Can you share examples of how you’ve communicated security strategy to boards or C-suites?”
5. Flexibility and engagement models
Different organizations need different levels of involvement. The right partner should offer flexible models, whether project-based, interim, or supplemental support, so you’re not locked into unnecessary costs.
Red flag: One-size-fits-all packages that force you into long-term contracts regardless of your maturity.
Ask: “How do you adjust your services as a client’s security program matures?”
6. Independence and objectivity
A vCISO’s value lies in impartial advice. If their business model depends heavily on reselling tools or technology, you might not get unbiased guidance.
Red flag: Their recommendations always point toward specific vendors or products they sell.
Ask: “How do you make sure your recommendations remain independent of vendor relationships?”
Your Next Move
The right Virtual CISO service can be a powerful growth enabler. Executives need partners who can cut through complexity, give them clear risk insights, and deliver measurable results.
That’s where Alpha Apex Group (AAG) excels. With rapid placement times, proprietary toolkits, and a proven consultative approach, AAG goes beyond technical checklists to embed security into business strategy.
For decision-makers who want cybersecurity leadership that drives trust as well as growth, AAG is the clear choice.
So, get in touch today to see how we can help.
FAQ: Finding the Right Virtual CISO Consulting Partner
1. What does a Virtual CISO consulting service actually do?
A vCISO provides executive-level guidance to design and run your cybersecurity program, from building policies and security controls to leading risk assessments, incident response, and regulatory compliance strategies, without the cost of a full-time hire.
2. Why not just hire an internal security leader instead of a vCISO?
For many organizations, hiring a permanent security leader takes months and can cost a lot of money. A vCISO gives you immediate access to seasoned security experts who can stabilize risk, build long-term strategies, and scale support as your needs evolve.
3. How do vCISO consulting services support regulatory compliance?
Experienced vCISOs know how to align your cybersecurity policies and security controls with frameworks like NIST, ISO, HIPAA, PCI, and GDPR. They actively design programs that make compliance sustainable year-round.
4. What kinds of businesses benefit most from a vCISO?
Any organization that handles sensitive data, faces growing threats, or operates in regulated industries can benefit. A vCISO helps bridge leadership gaps, prioritize investments in your cybersecurity program, and make sure you’re protected by the right mix of strategy, process, and security experts.


![Top 10 AI Executive Search Firms & Recruiters [2026 Update]](https://images.squarespace-cdn.com/content/v1/65bd0965904e7e695a70ed54/1739296788430-T30WVTQN5548FP3W15EU/Top+AI+Executive+Search+Firms+%26+Recruiters+%282%29.jpg)
















